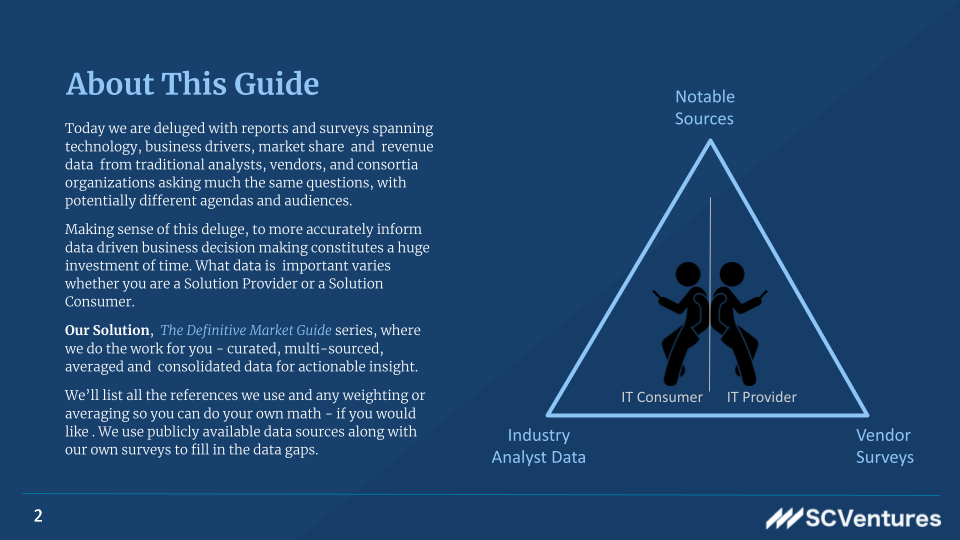
Description
With the adoption of the cloud and cloud-native architectural and development approaches the challenges facing securing of apps data and infrastructure continues to grow in complexity. From traditional challenges addressing identifying and responding to threats from vulnerabilities across open source and cloud infrastructure to remediation across the development and runtime environments related to delivering and maintaining secure applications in this new cloud native landscape. In this guide we look at the end-to-end picture of what is needed to define a cloud-native security strategy.
Cloud Native Security brings together a unique combination of existing and new approaches spanning vulnerabilities, code scanning including (I)nteractive (A)pplication (S)ecurity (P)rotection – IASP , (D)ynamic ASP, and (R)untime ASP to insuring Kubernetes and cloud configuration accuracy, container image lifecycle security as well as traditional virtual and physical application and infrastructure firewalls, micro-services API consistency etc.
This continues to grow in complexity as the interdependence between serverless application architectures and multi-vendor micro-service and private APIs open up new potential exploit paths.